|
|||||||||||||||||
|
|||||||||||||||||
|
Goal: Provide information technology (IT) infrastructure services to agencies and other government customers that are high quality, efficient, and add value |
|||||||||||||||||
|
Why
is this goal important? Managing a complex infrastructure for multiple agencies that is both reliable and secure is the business of the Office of Enterprise Technology. In some cases, the agency provides services directly. In other cases, OET's oversight functions (enterprise architecture, IT standards and purchasing and planning and program management) make the agency-based utility services of a caliber that allows state government to function efficiently and effectively.
What is OET doing to achieve
this goal?
How is OET's
progress?
Value |
|||||||||||||||||
|
Goal: Develop an enterprise security program to protect the integrity and confidentiality of data, and to ensure the continuous availability of critical government services |
|||||||||||||||||
|
Why is this goal important? The increase in security threats occurs at the same time that there is increasing demand from citizens for easy, accessible online service. The challenge faced by the state is how to safely and securely collect, store and protect the growing volumes of personal data and how to share that data effectively among governmental programs. In order to maintain citizen trust, the state must always balance ready access to government service and public information with its obligation to ensure that citizen interaction with government is safe, secure and confidential.
With start-up funding from the 2006 Legislature, the ESO has instituted and has begun to staff the following program areas: Planning and Preventive Controls:
Information Security Program development and management to provide an
understanding of the state's risk profile through risk management, policies,
standards, procedures, system certification and accreditation, awareness
training, emerging technology research, personnel and physical security.
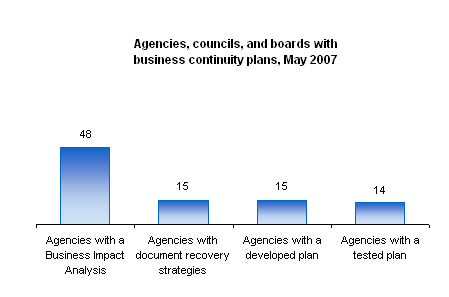
Threat and Vulnerability Management: Monitoring and evaluating the risk profiles of state entities and assets through the use of technology solutions that provide host scanning, penetration testing, threat dissemination and ongoing event monitoring. Investigative and Corrective Controls: Enterprise continuity management program for the delivery and recoverability of the state's key services, tied to incident response and computer forensics solutions. Information Security Compliance: The process to ensure that information security controls functions comply with applicable laws, regulations, and other requirements, working with state entities to develop cost-effective and sustainable solutions to mitigate compliance gaps. Access Control: Development and management of access control methodologies across state agencies and architecture for centralized controls to protect state assets. Small Agency Support: Security risk analysis, consulting services and access to enterprise security services for small agencies, boards and commissions that allow for cost-effective security solutions to support their business needs and meet Enterprise Security requirements. These program areas are in the active planning phase, which includes developing performance metrics that will measure on an ongoing basis the state's preparedness for security management and business continuity.
|
|||||||||||||||||
|
Goal: Ensure effective management of state technology investments and stewardship of state resources |
|||||||||||||||||
|
Why this is
goal important?
Prudent stewardship of the available, limited technology dollars is the only way the state can take effective advantage of the new technologies that are now available and are essential to improving the delivery of important government programs to citizens. Gone are the days when individual agencies could afford to "go it alone." There are too few skilled workers and available dollars to support redundancy in services that can be considered "utility," i.e., common to all government entities. The Office of Enterprise Technology provides leadership in the state's effort to leverage its IT investments, share precious resources, streamline systems and bring down their total cost of ownership (TCO) and engineer strategic benefits from the aggregation of goods and services.
What is
OET doing to achieve this goal?
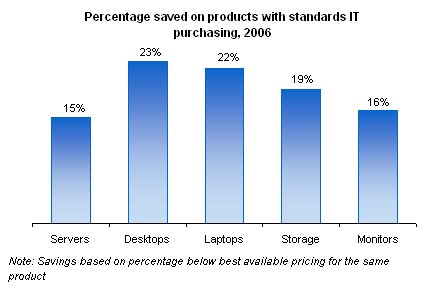
Consolidating
Utility Services. OET is leading an enterprise-wide effort to
consolidate those services that the state considers to be "utility
services," such as networking and email, that every
How is OET's progress?
|
|||||||||||||||||
|
Some images © 2003 www.clipart.com |
|||||||||||||||||
|



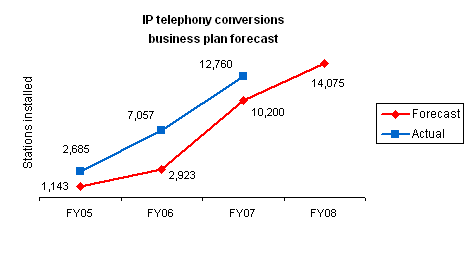 more features, the State of Minnesota has
increased the number of installed Internet Protocol (IP) telephones by
nearly 81 percent since July 2006 and is planning to add 1,315 lines (10.3
percent increase) in 2008. IP telephony (IPT) is a phone system that uses
voice-over internet protocol (VoIP) data connections to exchange voice data
that have been carried traditionally over the public switched telephone
system.
more features, the State of Minnesota has
increased the number of installed Internet Protocol (IP) telephones by
nearly 81 percent since July 2006 and is planning to add 1,315 lines (10.3
percent increase) in 2008. IP telephony (IPT) is a phone system that uses
voice-over internet protocol (VoIP) data connections to exchange voice data
that have been carried traditionally over the public switched telephone
system.


 agency needs to use but
does not need to manage and maintain independently.
agency needs to use but
does not need to manage and maintain independently.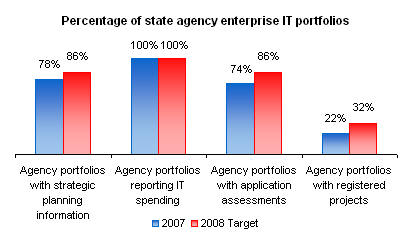 Portfolio Management.
Portfolio Management.